Preparing for the 300-215 CBRFIR (Conducting Forensic Analysis and Incident Response Using Cisco Technologies for CyberOps) exam requires a systematic and comprehensive study plan. Summarized lessons from 2023 achievers to help you prepare effectively for:
All 300-215 exam candidates should have their own study plan! All previous candidates who passed the exam have found their own learning methods, but the best solution is to practice a lot! Candidates who have taken multiple certification exams can skip directly to the following content! Use leads4pass 300-215 dumps: https://www.leads4pass.com/300-215.html(59 Q&A) to help you practice for the exam. If you are new, you can continue reading:
Experience sharing:
Understand the Exam Blueprint: Start by reviewing the official exam blueprint provided by Cisco. It outlines the topics and domains that will be covered in the exam. Familiarize yourself with the exam objectives to know what to expect.
Gather Study Materials: Collect the necessary study materials for the exam. This may include official Cisco documentation, recommended textbooks, online resources, and practice exams. Ensure you have access to up-to-date and relevant materials.
Set a Study Schedule: Plan your study schedule based on the time available until your exam date. Break down the topics into manageable study sessions, allotting more time to complex areas. Dedicate regular study periods to maintain consistency and avoid last-minute cramming.
Learn the Exam Topics:
a. Review CyberOps Principles: Understand the fundamentals of cybersecurity operations, incident response, and forensic analysis. Familiarize yourself with key concepts, terminology, and industry best practices.
b. Incident Response and Forensics: Study incident response procedures, incident handling, evidence collection, and analysis techniques. Focus on topics like network forensics, memory analysis, malware analysis, log analysis, and evidence preservation.
c. Network Intrusion Analysis: Learn how to analyze network traffic and detect intrusions using Cisco technologies. Study packet capture analysis, network protocols, security events, and analysis tools.
d. Incident Response and Handling: Understand incident response frameworks, processes, and methodologies. Familiarize yourself with incident response plans, roles and responsibilities, and incident containment strategies.
Hands-on Practice: Hands-on experience is crucial for this exam. Set up a lab environment using Cisco technologies or simulators to practice various forensic analysis and incident response scenarios. Perform tasks like packet capture analysis, log analysis, and malware analysis.
Take Practice Exams: Utilize practice exams to assess your knowledge and identify areas that require further study. Practice exams will help you get familiar with the exam format and timing, as well as improve your confidence and test-taking skills.
Join Study Groups or Forums: Engage with a community of learners by joining study groups or online forums dedicated to the 300-215 exam. Discussing topics, sharing resources, and clarifying doubts with fellow learners can enhance your understanding and provide valuable insights(Recommend: Quora, Facebook, Reddit…).
Review and Reinforce: As your exam date approaches, review all the topics you have studied. Focus on areas where you feel less confident or require additional reinforcement. Make use of flashcards or summary notes to reinforce key concepts.
Final Exam Preparation: In the last few days before the exam, practice with timed mock exams(leads4pass 300-215 dumps VCE) to simulate the real exam environment. Review your answers, identify weak areas, and allocate extra study time accordingly.
Exam Day: On the day of the exam, get a good night’s sleep, have a healthy breakfast, and arrive at the exam center well in advance. Stay calm, manage your time wisely during the exam, and carefully read each question before answering.
The above experience can solve most of the problems before your exam!
Continue reading! Get a free gift.
Latest Cisco 300-215 Exam Questions Online Practice Test
| From | Number of exam questions | Verify answer |
| leads4pass 300-215 dumps | 15 | Go |
Question 1:
What is the steganography anti-forensics technique?
A. hiding a section of a malicious file in unused areas of a file
B. changing the file header of a malicious file to another file type
C. sending malicious files over a public network by encapsulation
D. concealing malicious files in ordinary or unsuspecting places
https://blog.eccouncil.org/6-anti-forensic-techniques-that-every-cyber-investigator-dreads/
Question 2:
What are YARA rules based upon?
A. binary patterns
B. HTML code
C. network artifacts
D. IP addresses
Question 3:
An employee receives an email from a “trusted” person containing a hyperlink that is malvertising. The employee clicks the link and the malware downloads.
An information analyst observes an alert at the SIEM and engages the cybersecurity team to conduct an analysis of this incident in accordance with the incident response plan.
Which event detail should be included in this root cause analysis?
A. phishing email sent to the victim
B. alarm raised by the SIEM
C. information from the email header
D. alert identified by the cybersecurity team
Question 4:
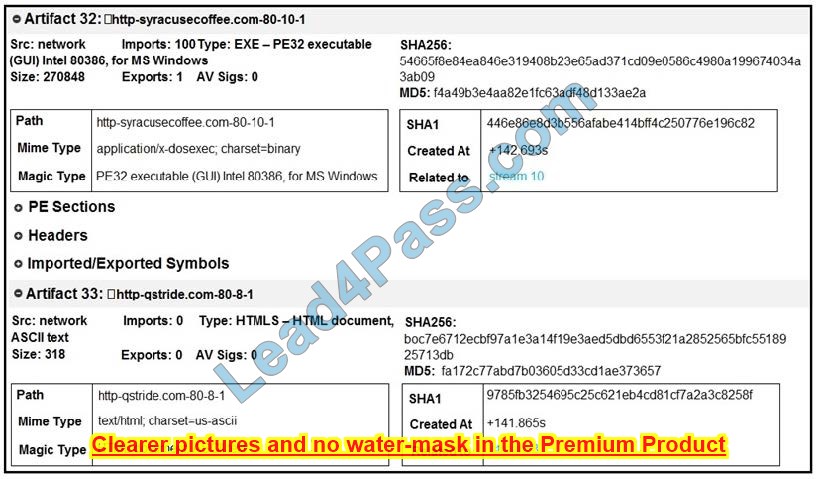
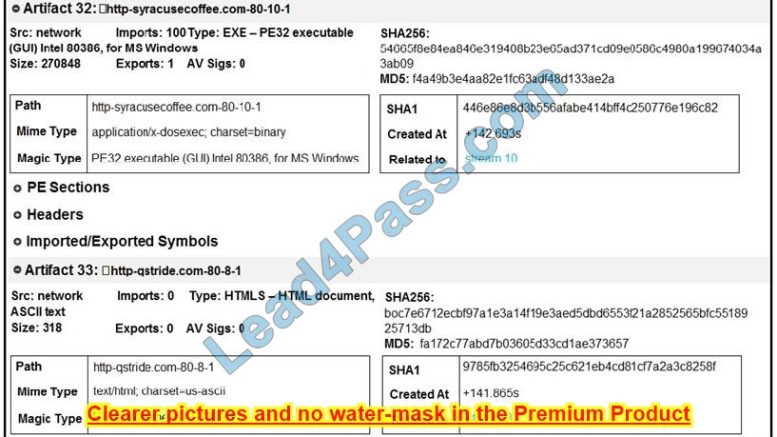
Refer to the exhibit. What do these artifacts indicate?
A. An executable file is requesting an application download.
B. A malicious file is redirecting users to different domains.
C. The MD5 of a file is identified as a virus and is being blocked.
D. A forged DNS request is forwarding users to malicious websites.
Question 5:
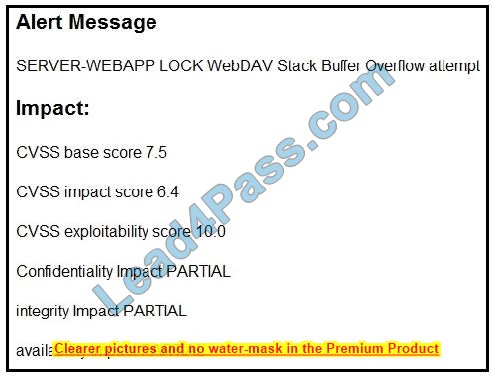
Refer to the exhibit. After a cyber-attack, an engineer is analyzing an alert that was missed on the intrusion detection system. The attack exploited a vulnerability in a business-critical, web-based application and violated its availability.
Which two migration techniques should the engineer recommend? (Choose two.)
A. encapsulation
B. NOP sled technique
C. address space randomization
D. heap-based security
E. data execution prevention
Question 6:
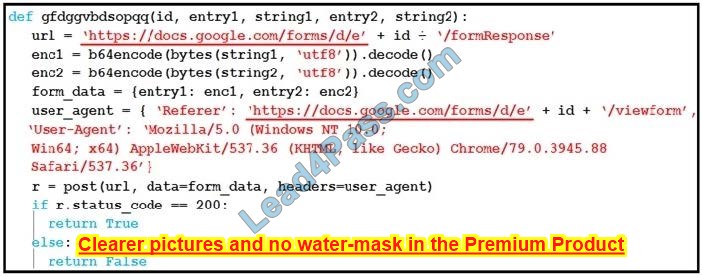
Refer to the exhibit. Which type of code is being used?
A. Shell
B. VBScript
C. BASH
D. Python
Question 7:
Which scripts will search a log file for the IP address of 192.168.100.100 and create an output file named parsed_host.log while printing results to the console?
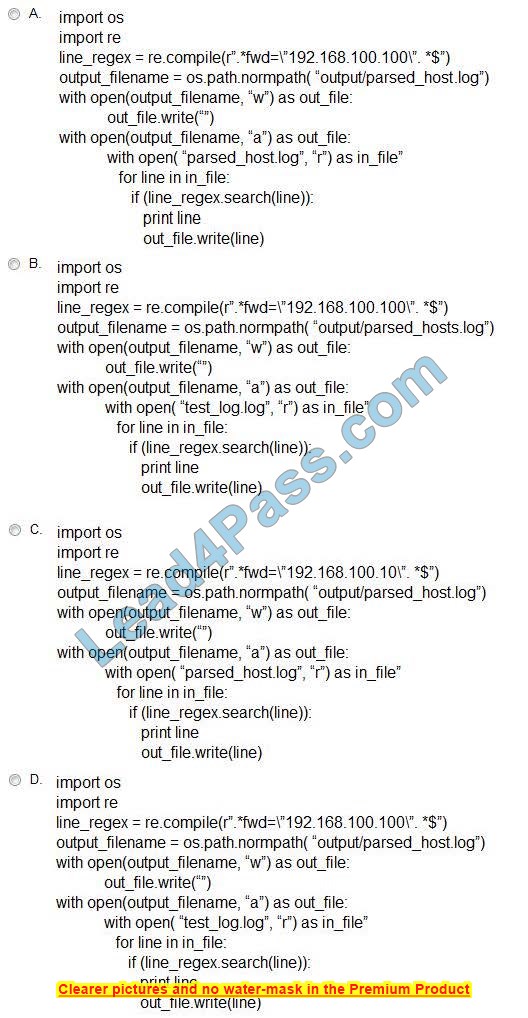
A. Option A
B. Option B
C. Option C
D. Option D
Question 8:
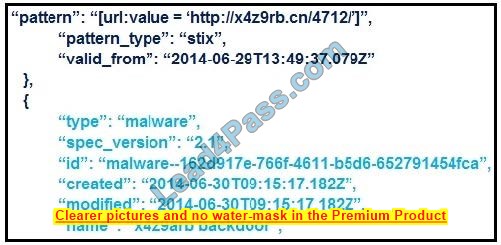
Refer to the exhibit. What is the IOC threat and URL in this STIX JSON snippet?
A. malware; `http://x4z9arb.cn/4712/\’
B. malware; x4z9arb backdoor
C. x4z9arb backdoor; http://x4z9arb.cn/4712/
D. malware; malware–162d917e-766f-4611-b5d6-652791454fca
E. stix; `http://x4z9arb.cn/4712/\’
Question 9:
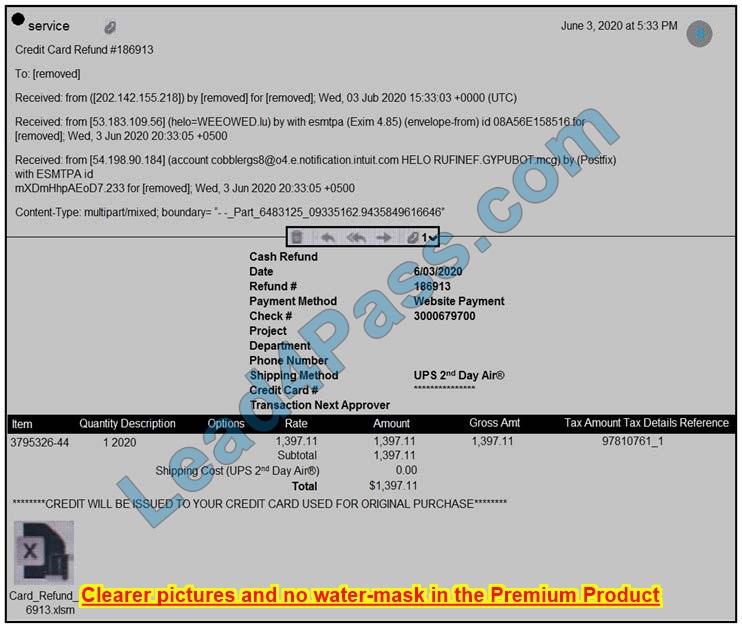
Refer to the exhibit. Which element in this email is an indicator of an attack?
A. IP Address: 202.142.155.218
B. Content-Type: multipart/mixed
C. attachment: “Card-Refund”
D. subject: “Service Credit Card”
Question 10:
Which magic byte indicates that an analyzed file is a pdf file?
A. cGRmZmlsZQ
B. 706466666
C. 255044462d
D. 0a0ah4cg
Question 11:
DRAG DROP
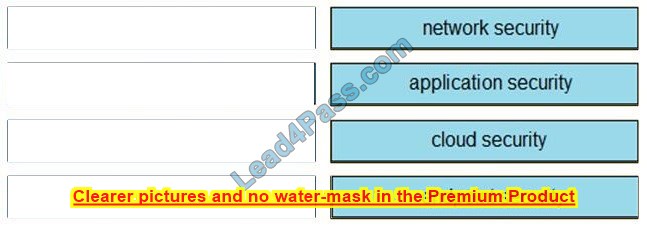
Drag and drop the capabilities on the left onto the Cisco security solutions on the right.
Select and Place:
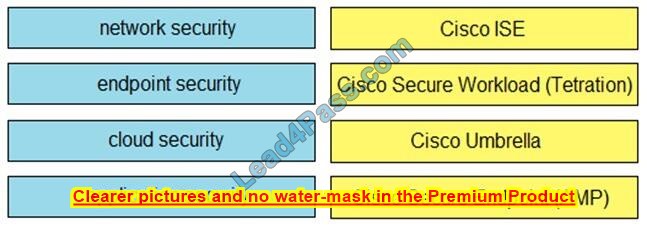
Correct Answer:
Question 12:
What is the function of a disassembler?
A. aids in performing static malware analysis
B. aids viewing and changing the running state
C. aids in transforming symbolic language into machine code
D. aids in defining breakpoints in program execution
Question 13:
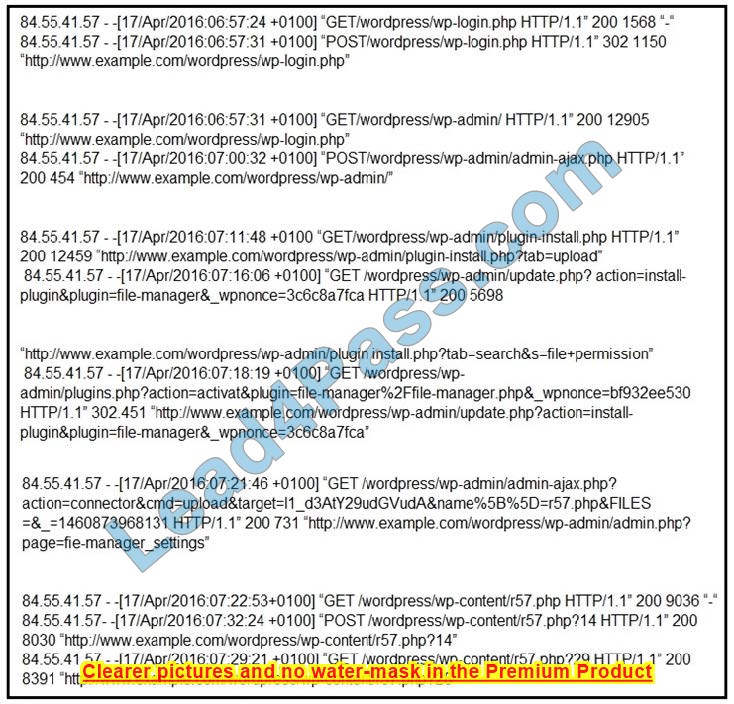
Refer to the exhibit. Which two determinations should be made about the attack from the Apache access logs? (Choose two.)
A. The attacker used the r57 exploit to elevate their privilege.
B. The attacker uploaded the word press file manager trojan.
C. The attacker performed a brute force attack against word press and used SQL injection against the backend database.
D. The attacker used the word press file manager plugin to upload r57.php.
E. The attacker logged on normally to word press admin page.
Question 14:
An engineer is investigating a ticket from the accounting department in which a user discovered an unexpected application on their workstation.
Several alerts are seen from the intrusion detection system of unknown outgoing internet traffic from this workstation.
The engineer also notices a degraded processing capability, which complicates the analysis process. Which two actions should the engineer take? (Choose two.)
A. Restore to a system recovery point.
B. Replace the faulty CPU.
C. Disconnect from the network.
D. Format the workstation drives.
E. Take an image of the workstation.
Question 15:
DRAG DROP
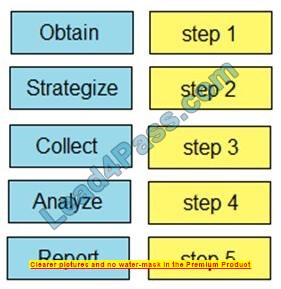
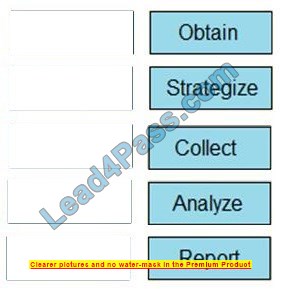
Drag and drop the steps from the left into the order to perform a forensics analysis of infrastructure networks on the right.
Select and Place:
Correct Answer:
…
Download 59 latest Cisco 300-215 exam questions and answers: https://www.leads4pass.com/300-215.html (300-215 dumps)
View answer:
| Number: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q12 | Q13 | Q14 |
| Answers: | A | A | B | A | CE | D | A | D | C | C | A | CD | AE |
These are the best Cisco 300-215 CBRFIR Exam Experience that I shared: part from the test experience of the successful ones and part from the 300-215 exam questions provided for free by leads4pass to help all candidates to plan for 2023 Cisco 300-215 Plan! Finally, I wish all candidates success in passing the 300-215 CBRFIR Exam.