The latest CAS-004 dumps are the best exam material for the “CompTIA Advanced Security Practitioner (CASP+)” 2023 certification exam.
leads4pass provides 334 latest exam questions and answers, download with PDF and VCE CAS-004 dumps: https://www.leads4pass.com/cas-004.html, practice the latest exam questions to help candidates pass the exam successfully.
Not only that, participate in the CAS-004 online practice test to verify your current strength and help you further improve yourself.
Practice the latest CAS-004 exam questions online
| Number of exam questions | Exam name | Exam code | From | Answers |
| 15 | CompTIA Advanced Security Practitioner (CASP+) | CAS-004 | leads4pass | View |
Question 1:
A company runs a well-attended, on-premises fitness club for its employees, about 200 of them each day. Employees want to sync the center\’s login and attendance program with their smartphones. Human resources, which manages the contract for the fitness center, has asked the security architecture to help draft security and privacy requirements.
Which of the following would BEST address these privacy concerns?
A. Use biometric authentication.
B. Utilize geolocation/geofencing.
C. Block unauthorized domain bridging.
D. Implement containerization
Question 2:
An analyst executes a vulnerability scan against an internet-facing DNS server and receives the following report:

Which of the following tools should the analyst use FIRST to validate the most critical vulnerability?
A. Password cracker
B. Port scanner
C. Account enumerator
D. Exploitation framework
Question 3:
A security engineer was auditing an organization\’s current software development practice and discovered that multiple open-source libraries were Integrated into the organization\’s software. The organization currently performs SAST and DAST on the software it develops.
Which of the following should the organization incorporate into the SDLC to ensure the security of the open-source libraries?
A. Perform additional SAST/DAST on the open-source libraries.
B. Implement the SDLC security guidelines.
C. Track the library versions and monitor the CVE website for related vulnerabilities.
D. Perform unit testing of the open-source libraries.
Reference: https://www.whitesourcesoftware.com/resources/blog/application-security-best-practices/
Question 4:
An application developer is including third-party background security fixes in an application. The fixes seem to resolve a currently identified security issue. However, when the application is released to the public, reports come In that a previous vulnerability has returned. Which of the following should the developer integrate into the process to BEST prevent this type of behavior?
A. Peer review
B. Regression testing
C. User acceptance
D. Dynamic analysis
Question 5:
A developer needs to provide feedback on a peer\’s work during the SDLC. While reviewing the code changes, the developer discovers session ID tokens for a web application will be transmitted over an insecure connection. Which of the following code snippets should the developer recommend implementing to correct the vulnerability?
A. Cookie cookie = new Cookie (“primary”); cookie.secure(true);
B. String input = request.getParameter (“input”); String character Pattern = “[./a-zA-ZO-9? “=” and]”; If (! input.matches (character Pattern)} { out.println (“Invalid Input”); )
C. 15
D. V>
Question 6:
An organization is researching the automation capabilities for systems within an OT network. A security analyst wants to assist with creating secure coding practices and would like to learn about the programming languages used on the PLCs. Which of the following programming languages is the MOST relevant for PLCs?
A. Ladder logic
B. Rust
C. C
D. Python
E. Java
Question 7:
A company has decided to move an ERP application to a public cloud vendor. The company wants to replicate some of its global policies from on-premises to the cloud. The policies include data encryption, token management, and limited user
access to the ERP application The Chief Information Officer (CIO) is mainly concerned about privileged accounts that might be compromised and used to alter data in the ERP application.
Which of the following is the BEST option to meet the requirements?
A. Sandboxing
B. CASB
C. MFA
D. Security as a service
Question 8:
SIMULATION
As a security administrator, you are asked to harden a server running Red Hat Enterprise Server 5.5 64-bit.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server. There are no wireless connections to the server, and it does not need to print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
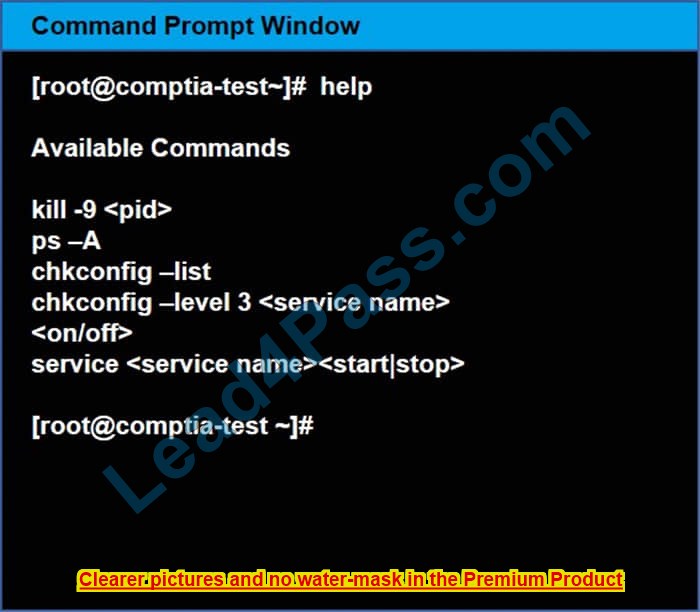
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Correct Answer: Check the answer in the explanation.
See the explanation below In Order to deactivate web services, database services, and print services, we can do the following things 1) deactivate its services /etc/init.d/apache2 stop /etc/init.d/mysqld stop 2) close ports for these services Web Server
iptables -I INPUT -p tcp -m tcp –dport 443 -j REJECTservice iptables save Print Server iptables -I INPUT -p tcp -m tcp –dport 631 -j REJECTservice iptables save
Database Server iptables -I INPUT -p tcp -m tcp –dport <> -j REJECTservice iptables save 3) Kill the process any running for the same ps -aef|grep mysql kill -9 <>
Question 9:
Security is assisting the marketing department with ensuring the security of the organization\’s social media platforms. The two main concerns are:
1.
The Chief marketing officer (CMO) email is being used department-wide as the username
2.
The password has been shared within the department
Which of the following controls would be BEST for the analyst to recommend?
A. Configure MFA for all users to decrease their reliance on other authentication.
B. Have periodic, scheduled reviews to determine which OAuth configurations are set for each media platform.
C. Create multiple social media accounts for all marketing users to separate their actions.
D. Ensure the password being shared is sufficient and not written down anywhere.
Question 10:
A company is looking for a solution to hide data stored in databases. The solution must meet the following requirements:
1.
Be efficient at protecting the production environment
2.
Not require any change to the application
3.
Act at the presentation layer
Which of the following techniques should be used?
A. Masking
B. Tokenization
C. Algorithmic
D. Random substitution
Question 11:
A company launched a new service and created a landing page within its website network for users to access the service. Per company policy, all websites must utilize encryption for any authentication pages. A junior network administrator proceeded to use an outdated procedure to order new certificates. Afterward, customers are reporting the following error when accessing a new web page: NET: ERR_CERT_COMMON_NAME_INVALID. Which of the following BEST describes what the administrator should do NEXT?
A. Request a new certificate with the correct subject alternative name that includes the new websites.
B. Request a new certificate with the correct organizational unit for the company\’s website.
C. Request a new certificate with a stronger encryption strength and the latest cipher suite.
D. Request a new certificate with the same information but including the old certificate on the CRL.
Question 12:
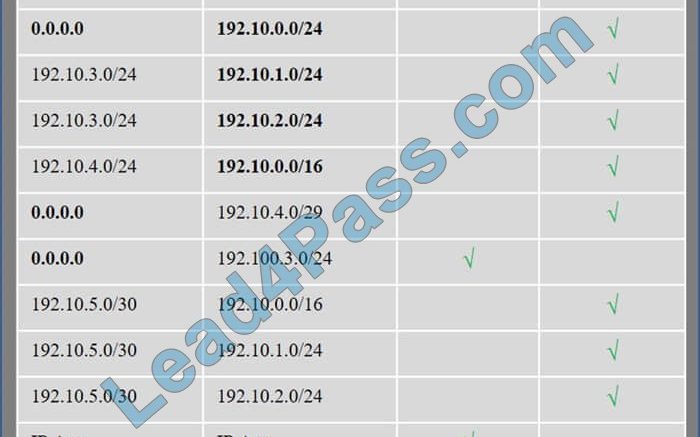
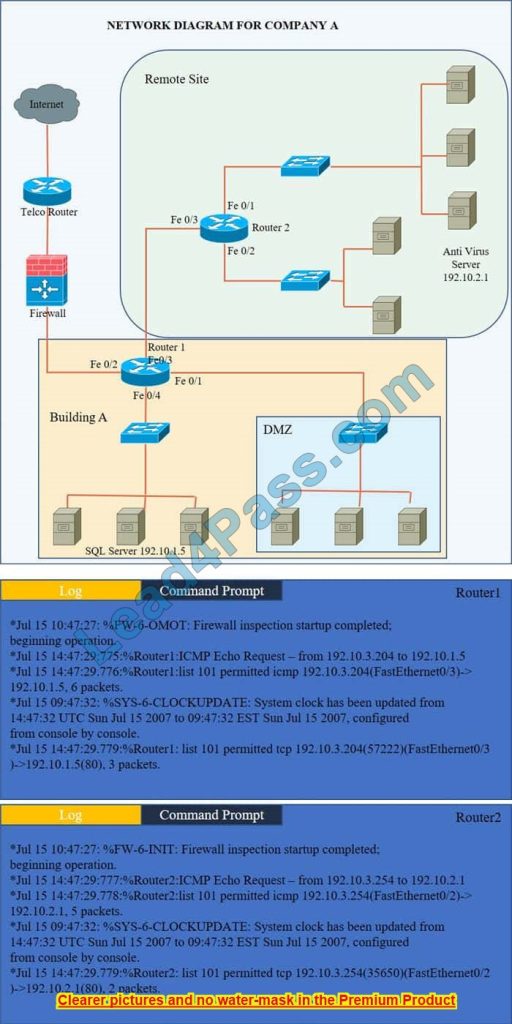
Company A has noticed abnormal behavior targeting their SQL server on the network from a rogue IP address. The company uses the following internal IP address ranges: 192.10.1.0/24 for the corporate site and 192.10.2.0/24 for the remote
site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.
Hot Area:
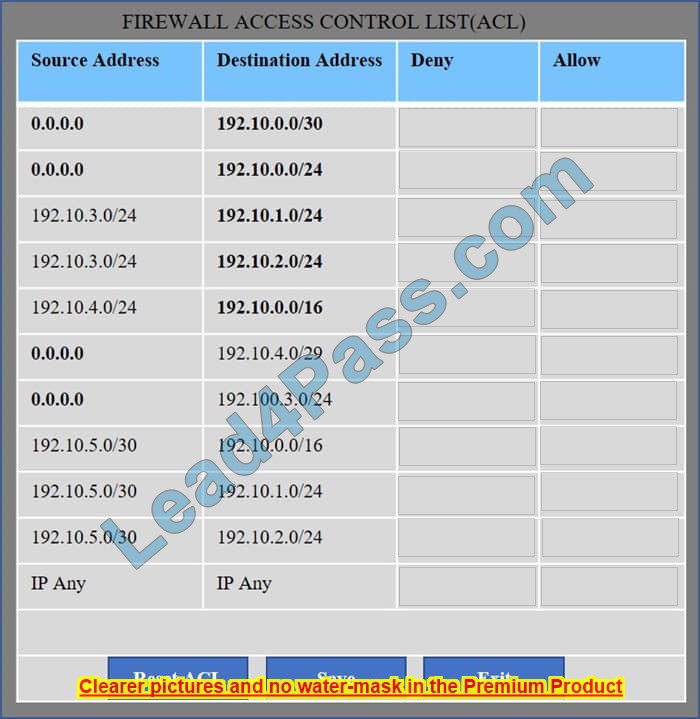
Correct Answer:
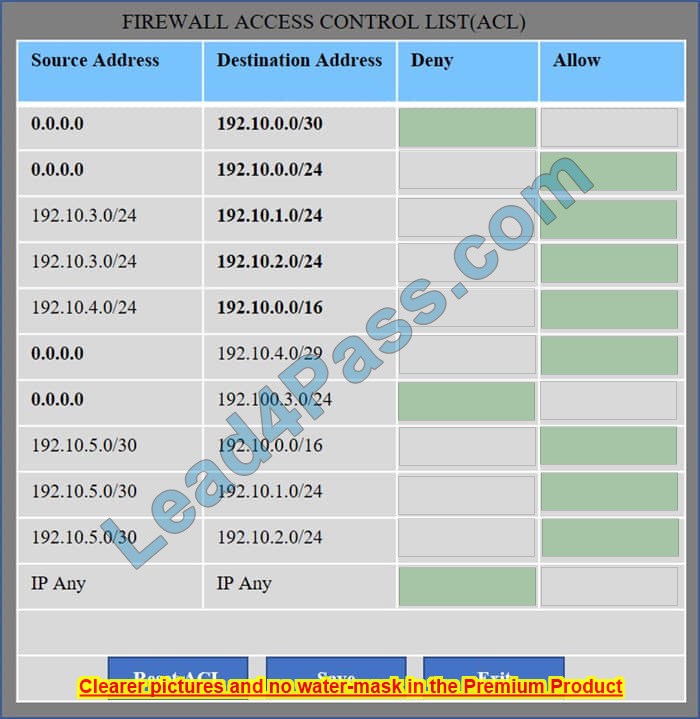
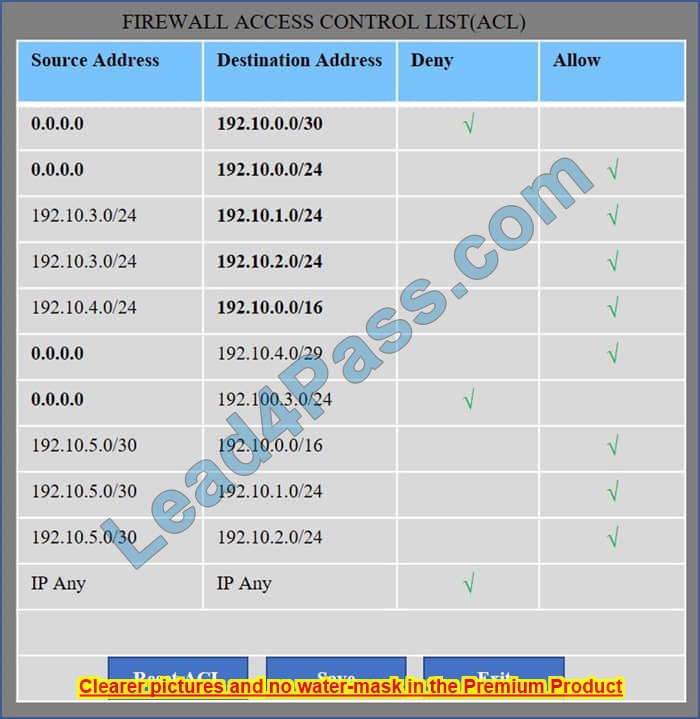
We have the traffic coming from two rogue IP addresses: 192.10.3.204 and 192.10.3.254 (both in the 192.10.30.0/24 subnet) going to IPs in the corporate site subnet (192.10.1.0/24) and the remote site subnet (192.10.2.0/24). We need to Deny (block) this traffic at the firewall by ticking the following two checkboxes:
Question 13:
a security analyst is validating the MAC policy on a set of Android devices The policy was written to ensure non-critical applications are unable to access certain resources. When reviewing dmesg, the analyst notes many entries, such as:
avc: denied { open } for pid=1018 comm= “ire” path= “/dev/if0″dev= “tmpfs” scontext=u:r:IRC:sO tcontext=u:object_r:default:s0tclass=chr_file permissive=l
Despite the denial message, this action was still permitted Which of the following is the MOST likely fix for this issue?
A. Add the objects of concern to the default context
B. Set the devices to enforcing mode
C. Create separate domain and context files for IRC
D. Rebuild the policy, reinstall, and test
Question 14:
An organization recently started processing, transmitting, and storing its customers’ credit card information. Within a week of doing so, the organization suffered a massive breach that resulted in the exposure of the customers’ information. Which of the following provides the BEST guidance for protecting such information while it is at rest and in transit?
A. NIST
B. GDPR
C. PCI DSS
D. ISO
Reference: https://en.wikipedia.org/wiki/Payment_Card_Industry_Data_Security_Standard
Question 15:
Which of the following is the BEST reason to implement a separation of duties policy?
A. It minimizes the risk of Dos due to continuous monitoring.
B. It eliminates the need to enforce the least privilege by logging all actions.
C. It increases the level of difficulty for a single employee to perpetrate fraud.
D. it removes barriers to collusion and collaboration between business units.
…
Verify answer:
| Questions: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| Answers: | A | A | D | A | A | A | D | LABS | A | A | D | IMAGE | B | C | A |
The above 15 latest CAS-004 exam questions and answers are shared for free. This is just to help candidates verify their current strengths.
Download the complete CAS-004 exam materials: https://www.leads4pass.com/cas-004.html, Help you simulate exercises more easily.
Summarize:
The “CompTIA Advanced Security Practitioner (CASP+)” certification exam remains one of the most popular CompTIA CASP+ certifications, so taking and passing it is something to celebrate, and we can imagine success in helping ourselves with Career prospects and the joy of increasing income.
Download CAS-004 dumps with the best materials of 2023: https://www.leads4pass.com/cas-004.html, and practice the latest and complete CAS-004 exam questions to help you pass the exam.