
The latest updated leads4pass 312-50v12 dumps for 2025: https://www.leads4pass.com/312-50v12.html, contains 596 real exam questions and answers, verified by a professional team, to help you pass the CEH v12 certification exam.
Passing the EC-COUNCIL 312-50v12 exam is not that simple, you need to go through a lot of practice and preparation before the exam to be really successful, use leads4pass 312-50v12 dumps with PDF and VCE to help you complete all the exercises.
2025 New EC-COUNCIL 312-50v12 dumps Exam Questions and Answers from leads4pass
| Type | Number of exam questions | Exam name | Exam code | Latest updated | Release time |
| Free | 15 | Certified Ethical Hacker Exam (CEHv12) | 312-50v12 | 312-50v11 dumps | 12/31/2024 |
New Question 1:
You are a cybersecurity specialist at CloudTech Inc., a company providing cloud-based services. You are managing a project for a client who wants to migrate their sensitive data to a public cloud service. To comply with regulatory requirements, the client insists on maintaining full control over the encryption keys even when the data is at rest on the cloud. Which of the following practices should you implement to meet this requirement?
A. Use the cloud service provider\’s encryption services but store keys on-premises.
B. Use the cloud service provider\’s default encryption and key management services.
C. Rely on Secure Sockets Layer (SSL) encryption for data at rest.
D. Encrypt data client-side before uploading to the cloud and retain control of the encryption keys.
Correct Answer: D
The best practice to meet the client\’s requirement is to encrypt data client- side before uploading to the cloud and retain control of the encryption keys. This practice is also known as client-side encryption or end-to-end encryption, and it involves encrypting the data on the client\’s device using a software or hardware tool that generates and manages the encryption keys. The encrypted data is then uploaded to the cloud service, where it remains encrypted at rest. The encryption keys are never shared with the cloud service provider or any third party, and they are only used by the client to decrypt the data when needed. This way, the client can maintain full control over the encryption keys and the security of the data, even when the data is stored on a public cloud service12. The other options are not as optimal as option D for the following reasons:
A. Use the cloud service provider\’s encryption services but store keys on- premises: This option is not feasible because it contradicts the client\’s requirement of maintaining full control over the encryption keys. Using the cloud service provider\’s encryption services means that the client has to rely on the cloud service provider to generate and manage the encryption keys, even if the keys are stored on-premises. The cloud service provider may have access to the keys or the ability to decrypt the data, which may compromise the security and privacy of the data. Moreover, storing the keys on-premises may introduce additional challenges, such as key distribution, synchronization, backup, and recovery3. B. Use the cloud service provider\’s default encryption and key management services: This option is not desirable because it violates the client\’s requirement of maintaining full control over the encryption keys. Using the cloud service provider\’s default encryption and key management services means that the client has to trust the cloud service provider to encrypt and decrypt the data on the server-side, using the cloud service provider\’s own encryption keys and mechanisms. The cloud service provider may have access to the keys or the ability to decrypt the data, which may compromise the security and privacy of the data. Furthermore, the cloud service provider\’s default encryption and key management services may not meet the regulatory requirements or the security standards of the client4. C. Rely on Secure Sockets Layer (SSL) encryption for data at rest: This option is not sufficient because SSL encryption is not designed for data at rest, but for data in transit. SSL encryption is a protocol that encrypts the data as it travels over the internet between the client and the server, using certificates and keys that are exchanged and verified by both parties. SSL encryption can protect the data from being intercepted or modified by unauthorized parties, but it does not protect the data from being accessed or decrypted by the cloud service provider or any third party who has access to the server. Moreover, SSL encryption does not provide the client with any control over the encryption keys or the security of the data. References:
1: Client-side encryption – Wikipedia
2: What is Client-Side Encryption? | Definition, Benefits and Best Practices | Kaspersky
3: Cloud Encryption Key Management: What You Need to Know | Thales
4: Cloud Encryption: How It Works and How to Use It | Comparitech : What is SSL Encryption and How Does it Work? | Norton
New Question 2:
You are the lead cybersecurity analyst at a multinational corporation that uses a hybrid encryption system to secure inter-departmental communications. The system uses RSA encryption for key exchange and AES for data encryption, taking advantage of the strengths of both asymmetric and symmetric encryption. Each RSA key pair has a size of \’n\’ bits, with larger keys providing more security at the cost of slower performance. The time complexity of generating an RSA key pair is O(n^2), and AES encryption has a time complexity of O(n). An attacker has developed a quantum algorithm with time complexity O((log n)^2) to crack RSA encryption. Given \’n=4000\’ and variable \’AES key size\’, which scenario is likely to provide the best balance of security and performance?
A. AES key size=128 bits: This configuration provides less security than option A, but RSA key generation and AES encryption will be faster.
B. AES key size=256 bits: This configuration provides a high level of security, but RSA key generation may be slow.
C. AES key size=192 bits: This configuration is a balance between options A and B, providing moderate security and performance.
D. AES key size=512 bits: This configuration provides the highest level of security but at a significant performance cost due to the large AES key size.
Correct Answer: C
https://www.techtarget.com/searchsecurity/definition/Advanced-Encryption-Standard
New Question 3:
Abel, a cloud architect, uses container technology to deploy applications/software including all its dependencies, such as libraries and configuration files, binaries, and other resources that run independently from other processes in the cloud environment. For the containerization of applications, he follows the five-tier container technology architecture. Currently. Abel is verifying and validating image contents, signing images, and sending them to the registries. Which of the following tiers of the container technology architecture is Abel currently working in?
A. Tier-1: Developer machines
B. Tier-4: Orchestrators
C. Tier-3: Registries
D. Tier-2: Testing and accreditation systems
Correct Answer: D
The official management decision given by a senior agency official to authorize operation of an information system and to explicitly accept the risk to agency operations (including mission, functions, image, or reputation), agency assets, or individuals, based on the implementation of an agreed-upon set of security controls. formal declaration by a designated accrediting authority (DAA) or principal accrediting authority (PAA) that an information system is approved to operate at an acceptable level of risk, based on the implementation of an approved set of technical, managerial, and procedural safeguards. See authorization to operate (ATO). Rationale: The Risk Management Framework uses a new term to refer to this concept, and it is called authorization. Identifies the information resources covered by an accreditation decision, as distinguished from separately accredited information resources that are interconnected or with which information is exchanged via messaging. Synonymous with Security Perimeter. For the purposes of identifying the Protection Level for confidentiality of a system to be accredited, the system has a conceptual boundary that extends to all intended users of the system, both directly and indirectly connected, who receive output from the system. See authorization boundary. Rationale: The Risk Management Framework uses a new term to refer to the concept of accreditation, and it is called authorization. Extrapolating, the accreditation boundary would then be referred to as the authorization boundary.
New Question 4:
While performing an Nmap scan against a host, Paola determines the existence of a firewall. In an attempt to determine whether the firewall is stateful or stateless, which of the following options would be best to use?
A. -sA
B. -sX
C. -sT
D. -sF
Correct Answer: A
New Question 5:
Sarah, a system administrator, was alerted of potential malicious activity on the network of her company. She discovered a malicious program spread through the instant messenger application used by her team. The attacker had obtained access to one of her teammate\’s messenger accounts and started sending files across the contact list. Which best describes the attack scenario and what measure could have prevented it?
A. Instant Messenger Applications; verifying the sender\’s identity before opening any files.
B. Insecure Patch Management; updating application software regularly.
C. Rogue/Decoy Applications; ensuring software is labeled as TRUSTED.
D. Portable Hardware Media/Removable Devices; disabling Autorun functionality.
Correct Answer: A
The attack scenario is best described as Instant Messenger Applications, and the measure that could have prevented it is verifying the sender\’s identity before opening any files. Instant Messenger Applications are communication tools that allow users to exchange text, voice, video, and file messages in real time. However, they can also be used as attack vectors for spreading malware, such as viruses, worms, or Trojans, by exploiting the trust and familiarity between the users. In this scenario, the attacker compromised one of the team member\’s messenger account and used it to send malicious files to the other team members, who may have opened them without suspicion, thus infecting their systems. This type of attack is also known as an instant messaging worm. To prevent this type of attack, the users should verify the sender\’s identity before opening any files sent through instant messenger applications. This can be done by checking the sender\’s profile, asking for confirmation, or using a secure channel. Additionally, the users should also follow other security tips, such as using strong passwords, updating the application software, scanning the files with antivirus software, and reporting any suspicious activity. References:
1: Instant Messaging Worm – Techopedia
2: Cybersecurity\’s Silent Foe: A Comprehensive Guide to Computer Worms | Silent Quadrant
3: Instant Messenger Hacks: 10 Security Tips to Protect Yourself – MUO
4: Increased phishing attacks on instant messaging platforms: how to prevent them | Think Digital Partners
New Question 6:
What kind of detection techniques is being used in antivirus softwares that identifies malware by collecting data from multiple protected systems and instead of analyzing files locally it\’s made on the premiers environment?
A. VCloud based
B. Honypot based
C. Behaviour based
D. Heuristics based
Correct Answer: A
New Question 7:
Infecting a system with malware and using phishing to gain credentials to a system or web application are examples of which phase of the ethical hacking methodology?
A. Reconnaissance
B. Maintaining access
C. Scanning
D. Gaining access
Correct Answer: D
This phase having the hacker uses different techniques and tools to realize maximum data from the system. they\’re Password cracking ?Methods like Bruteforce, dictionary attack, rule-based attack, rainbow table are used. Bruteforce is trying all combinations of the password. Dictionary attack is trying an inventory of meaningful words until the password matches. Rainbow table takes the hash value of the password and compares with pre-computed hash values until a match is discovered.?Password attacks ?Passive attacks like wire sniffing, replay attack. Active online attack like Trojans, keyloggers, hash injection, phishing. Offline attacks like pre-computed hash, distributed network and rainbow. Non electronic attack like shoulder surfing, social engineering and dumpster diving.
New Question 8:
SQL injection (SQLi) attacks attempt to inject SQL syntax into web requests, which may Bypass authentication and allow attackers to access and/or modify data attached to a web application. Which of the following SQLI types leverages a database server\’s ability to make DNS requests to pass data to an attacker?
A. Union-based SQLI
B. Out-of-band SQLI
C. ln-band SQLI
D. Time-based blind SQLI
Correct Answer: B
Out-of-band SQL injection occurs when an attacker is unable to use an equivalent channel to launch the attack and gather results. … Out-of-band SQLi techniques would believe the database server\’s ability to form DNS or HTTP requests to deliver data to an attacker. Out-of-band SQL injection is not very common, mostly because it depends on features being enabled on the database server being used by the web application. Out-of- band SQL injection occurs when an attacker is unable to use the same channel to launch the attack and gather results. Out-of-band techniques, offer an attacker an alternative to inferential time-based techniques, especially if the server responses are not very stable (making an inferential time-based attack unreliable). Out-of-band SQLi techniques would rely on the database server\’s ability to make DNS or HTTP requests to deliver data to an attacker. Such is the case with Microsoft SQL Server\’s xp_dirtree command, which can be used to make DNS requests to a server an attacker controls; as well as Oracle Database\’s UTL_HTTP package, which can be used to send HTTP requests from SQL and PL/SQL to a server an attacker controls.
New Question 9:
What is the following command used for?
sqlmap.py-u ,,http://10.10.1.20/?p=1andforumaction=search” -dbs
A. Creating backdoors using SQL injection
B. A Enumerating the databases in the DBMS for the URL
C. Retrieving SQL statements being executed on the database
D. Searching database statements at the IP address given
Correct Answer: A
New Question 10:
Study the snort rule given below:
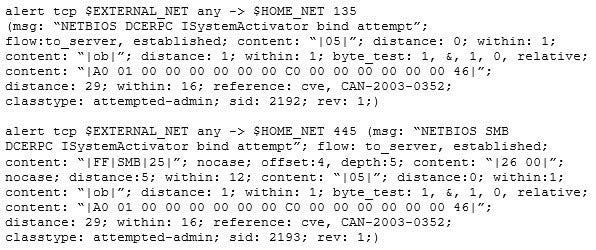
From the options below, choose the exploit against which this rule applies.
A. WebDav
B. SQL Slammer
C. MS Blaster
D. MyDoom
Correct Answer: C
New Question 11:
Attacker Rony Installed a rogue access point within an organization\’s perimeter and attempted to Intrude into its internal network. Johnson, a security auditor, identified some unusual traffic in the internal network that is aimed at cracking the authentication mechanism. He immediately turned off the targeted network and tested for any weak and outdated security mechanisms that are open to attack. What is the type of vulnerability assessment performed by Johnson in the above scenario?
A. Distributed assessment
B. Wireless network assessment
C. Most-based assessment
D. Application assessment
Correct Answer: B
Expanding your network capabilities are often done well using wireless networks, but it also can be a source of harm to your data system . Deficiencies in its implementations or configurations can allow tip to be accessed in an unauthorized manner.This makes it imperative to closely monitor your wireless network while also conducting periodic Wireless Network assessment.It identifies flaws and provides an unadulterated view of exactly how vulnerable your systems are to malicious and unauthorized accesses.Identifying misconfigurations and inconsistencies in wireless implementations and rogue access points can improve your security posture and achieve compliance with regulatory frameworks.
New Question 12:
Suppose your company has just passed a security risk assessment exercise. The results display that the risk of the breach in the main company application is 50%. Security staff has taken some measures and implemented the necessary controls. After that, another security risk assessment was performed showing that risk has decreased to 10%. The risk threshold for the application is 20%. Which of the following risk decisions will be the best for the project in terms of its successful continuation with the most business profit?
A. Accept the risk
B. Introduce more controls to bring risk to 0%
C. Mitigate the risk
D. Avoid the risk
Correct Answer: A
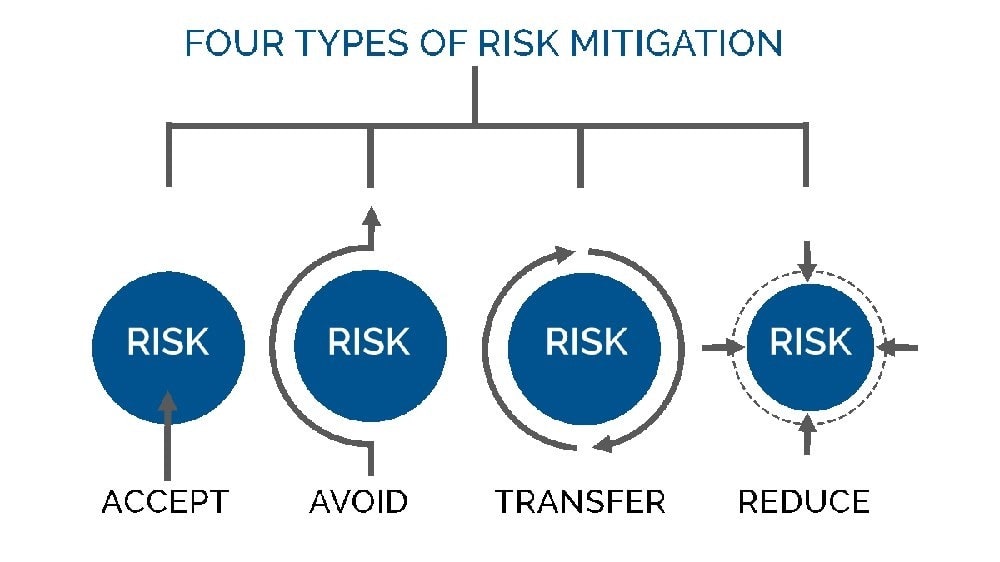
Risk Mitigation Risk mitigation can be defined as taking steps to reduce adverse effects. There are four types of risk mitigation strategies that hold unique to Business Continuity and Disaster Recovery. When mitigating risk, it\’s important to develop a strategy that closely relates to and matches your company\’s profile.
A picture containing diagram
Risk Acceptance
Risk acceptance does not reduce any effects; however, it is still considered a strategy. This strategy is a common option when the cost of other risk management options such as avoidance or limitation may outweigh the cost of the risk itself.
A company that doesn\’t want to spend a lot of money on avoiding risks that do not have a high possibility of occurring will use the risk acceptance strategy.
Risk Avoidance
Risk avoidance is the opposite of risk acceptance. It is the action that avoids any exposure to the risk whatsoever. It\’s important to note that risk avoidance is usually the most expensive of all risk mitigation options.
Risk Limitation
Risk limitation is the most common risk management strategy used by businesses. This strategy limits a company\’s exposure by taking some action. It is a strategy employing a bit of risk acceptance and a bit of risk avoidance or an average
of both. An example of risk limitation would be a company accepting that a disk drive may fail and avoiding a long period of failure by having backups.
Risk Transference
Risk transference is the involvement of handing risk off to a willing third party. For example, numerous companies outsource certain operations such as customer service, payroll services, etc. This can be beneficial for a company if a
transferred risk is not a core competency of that company. It can also be used so a company can focus more on its core competencies.
New Question 13:
Allen, a professional pen tester, was hired by XpertTech Solutions to perform an attack simulation on the organization\’s network resources. To perform the attack, he took advantage of the NetBIOS API and targeted the NetBIOS service. By
enumerating NetBIOS, he found that port 139 was open and could see the resources that could be accessed or viewed on a remote system. He came across many NetBIOS codes during enumeration.
Identify the NetBIOS code used for obtaining the messenger service running for the logged-in user?
A. <1B>
B. <00>
C. <03>
D. <20>
Correct Answer: C
<03>Windows Messenger administrationCourier administration is an organization based framework notice Windows administration by Microsoft that was remembered for some prior forms of Microsoft Windows. This resigned innovation,
despite the fact that it has a comparable name, isn\’t connected in any capacity to the later, Internet-based Microsoft Messenger administration for texting or to Windows Messenger and Windows Live Messenger (earlier named MSN
Messenger) customer programming.
The Messenger Service was initially intended for use by framework managers to tell Windows clients about their networks.[1] It has been utilized malevolently to introduce spring up commercials to clients over the Internet (by utilizing mass-
informing frameworks which sent an ideal message to a predetermined scope of IP addresses). Despite the fact that Windows XP incorporates a firewall, it isn\’t empowered naturally. Along these lines, numerous clients got such messages.
Because of this maltreatment, the Messenger Service has been debilitated as a matter of course in Windows XP Service Pack 2.
New Question 14:
What type of virus is most likely to remain undetected by antivirus software?
A. Cavity virus
B. Stealth virus
C. File-extension virus
D. Macro virus
Correct Answer: B
New Question 15:
In this attack, a victim receives an e-mail claiming from PayPal stating that their account has been disabled and confirmation is required before activation. The attackers then scam to collect not one but two credit card numbers, ATM PIN
number and other personal details. Ignorant users usually fall prey to this scam.
Which of the following statement is incorrect related to this attack?
A. Do not reply to email messages or popup ads asking for personal or financial information
B. Do not trust telephone numbers in e-mails or popup ads
C. Review credit card and bank account statements regularly
D. Antivirus, anti-spyware, and firewall software can very easily detect these type of attacks
E. Do not send credit card numbers, and personal or financial information via e-mail
Correct Answer: D
…
Get the latest updated 312-50v12 dumps for 2025: https://www.leads4pass.com/312-50v12.html (596 Q&A PDF +VCE).
EC-Council Certified Ethical Hacker (C|EH v12) Latest News
What is the goal of learning Certified Ethical Hacking (v12)
- Gain foundational knowledge of cybersecurity concepts: Understand key principles like vulnerability assessment, penetration testing, and risk management.
- Learn ethical hacking methodologies: Acquire practical skills in identifying system vulnerabilities, attack vectors, and potential threats.
- Develop skills in using ethical hacking tools: Become familiar with commonly used tools and techniques for network scanning, enumeration, system hacking, and more.
- Prepare for a career in cybersecurity: The CEH certification can enhance career prospects in roles like Security Analyst, Penetration Tester, and Cybersecurity Consultant.
- Improve organizational security posture: By understanding how attackers operate, individuals can help their organizations identify and mitigate security risks.
In essence, CEH v12 aims to provide a comprehensive understanding of cybersecurity threats and equip individuals with the knowledge and skills to proactively defend against them.
Certified Ethical Hacking (v12) Changes 2025
Pay attention to (CEH) v12. Every change has a vital role in your next arrangement. Here are some key changes:
In 2025, the Certified Ethical Hacking (CEH) program is transitioning to CEHv13 with a new learning framework.
Here are some key anticipated changes:
- Updated Content: Coverage will likely reflect the evolving threat landscape, including new attack vectors, vulnerabilities, and technologies like AI/ML, IoT, and cloud computing.
- Refreshed Methodology: The new framework may introduce a more structured and streamlined approach to ethical hacking methodologies.
- Enhanced Practical Skills: The focus on hands-on experience and practical skills development is expected to be further emphasized.
- Improved Alignment with Industry Standards: CEHv13 will likely be better aligned with current industry best practices, frameworks, and certifications.
Disclaimer: This information is based on general trends and expectations. The specific changes to CEHv13 may vary.
