leads4pass has shared the latest 300-915 dumps exam questions and answers more than once, and today continues to share some free 300-915 exam questions and answers to help all candidates progress.
leads4pass has also helped candidates pass the Cisco Certified DevNet Professional 300-915 Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT) certification exam more than once because they use Full 300-915 dumps with PDF and VCE: https://www.leads4pass.com/300-915.html (59 Q&A).
Check out the Cisco Certified DevNet Professional 300-915 PDF exam questions and answers shared for free: https://drive.google.com/file/d/1PSiCxtGU6gJDUSNO-wb9h0jlVetNDrpq/
Read the Cisco Certified DevNet Professional 300-915 exam questions and answers shared online today:
| Number of exam questions | Exam name | From | Release time | Previous issue |
| 15 | Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT) | leads4pass | Nov 04, 2022 | 300-915 dumps questions 16-30 |
New Question 31:
A company is collecting data from several thousand machines globally. Which software component in the overall architecture is the next destination of the dataflow after the data has been gathered and normalized on the edge data software?
A. relational database: MySQL
B. historian database: influxDB
C. message broker: Apache Kafka
D. dashboard: Node.js web app
Correct Answer: B
New Question 32:
Which data visualization technique should be used to represent an important single metric on a dashboard?
A. heatmap
B. scatter pot
C. gauge
D. treemap
Correct Answer: C
New Question 33:
Which two states are applications expected to be seen in when they are managed on Cisco IOx? (Choose two.)
A. DEACTIVATED
B. ACTIVATED
C. ALLOWED
D. STOPPED
E. VALIDATED
Correct Answer: BD
New Question 34:
Which connector is southbound?
A. horizontal connector
B. cloud connector
C. device connector
D. universal connector
Correct Answer: C
New Question 35:
An IoT engineer is responsible for security at an organization. Humans and machines need to be allowed to access services like database or computing on AWS. The engineer decides to implement dynamic secrets.
Which method helps to get this implementation accurate from a security point of view?
A. Create a central secret system for humans and machines to obtain very short-lived dynamic secrets to access any service.
B. Humans cannot be trusted, and each time they authenticate they should be issued with dynamic secrets. Machines can be trusted, and they can be issued with static credentials.
C. Maintain a different service associated with secret systems to issue access.
D. After a user is authenticated by any trusted system, the user can be trusted to use any service.
Correct Answer: A
New Question 36:
Which statement explains the correct position of a PLC within the CPwE architecture?
A. PLCs are always part of Level 0 ? process control.
B. PLCs are part of Level 4 ? site business planning.
C. PLCs are part of Level 1 ? basic control.
D. PLCs are placed at Level 2 ? area supervisory control.
Correct Answer: C
New Question 37:
A sensor reads potentially critical data from an industrial device, but most of the data from the sensor are not critical information and does not change unless a critical event happens.
Which data workflow is appropriate for how the critical and non-critical data are processed?
A.
1. Acquire sensor data.
2. Filter non-actionable data.
3. Perform action on data.
4. Send critical data and action performed on data to the cloud for storing.
B.
1. Acquire sensor data.
2. Send data to the cloud for processing and to determine action.
3. Send required action back to edge for action completion.
4. Perform action on data.
C.
1. Acquire sensor data.
2. Filter non-actionable data.
3. Perform action on data.
D.
1. Acquire sensor data.
2. Perform action on data.
3. Send data and action performed on data to the cloud for recording.
Correct Answer: D
New Question 38:
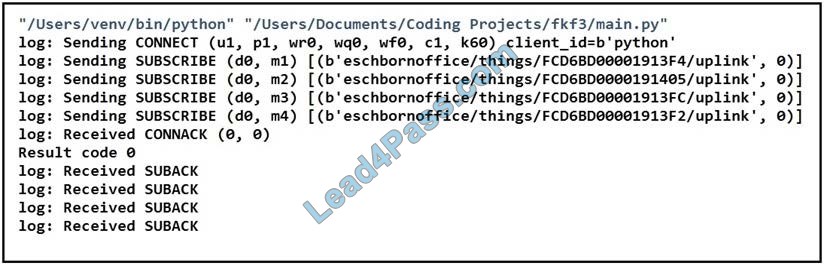
Refer to the exhibit. Which two statements about MQTT messaging are true? (Choose two.)
A. Result from code 5 means the connection is accepted; result code 0 means the connection is “refused, not authorized”.
B. Redundant ClientIDs are supported by MQTT brokers.
C. MQTT does not support a “keep alive” functionality because it runs on top of TCP.
D. Result code 0 means the connection is accepted; result code 5 means the connection is “refused, not authorized”.
E. Brokers can send the Last Will and Testament messages on behalf of the client.
Correct Answer: DE
New Question 39:
An IoT application has been built into the application CI/CD pipeline. The application needs credentials to access other applications, APIs, and cloud resources.
When should the credentials be inserted into the application using the CI/CD process?
A. hard coded into your application code base
B. during application runtime
C. after application testing
D. during application build time
Correct Answer: A
New Question 40:
Which two statements about how to provision and manage data originators in a cloud environment are true? (Choose two.)
A. The provisioning of digital identities is the responsibility of the data originators.
B. Cloud providers offer services for automated device provisioning, which allows the lifecycle of the cloud representation for data originators to be managed.
C. Cloud providers offer application programming interfaces, which allow programmatic provisioning of data originators.
D. There is no need to provision and manage access for data originators in the cloud.
E. access to public clouds must be configured and managed manually.
Correct Answer: CE
New Question 41:
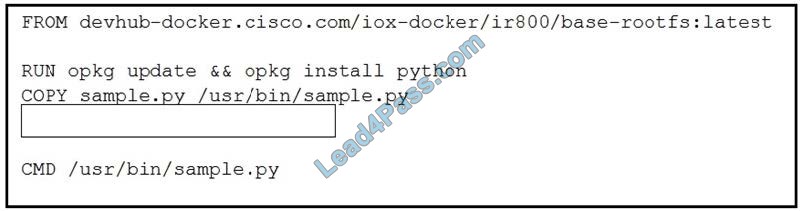
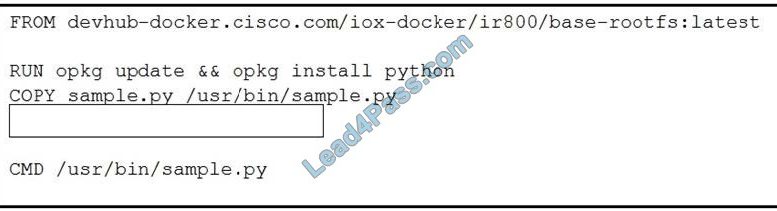
Refer to the exhibit. Which line of code completes the Dockerfile?
A. RUN chmod 777 /usr/bin/sample.py
B. RUN chown root: root /usr/bin/sample.py
C. WORKDIR /usr/bin
D. USER root
Correct Answer: A
Question 42:
A network is being configured for an Ethernet-connected sensor. The sensor fails to send data to the configured destination. The IP address of the sensor can be pinged from a laptop on the same subnet. When a different subnet is used, the sensor cannot be reached, but other clients on the same subnet are still accessible.
What are two reasons for the connectivity problem? (Choose two.)
A. wrong DNS server on the sensor
B. wrong subnet mask on your laptop
C. wrong default gateway on the sensor
D. wrong default gateway on your laptop
E. wrong subnet mask on the sensor
Correct Answer: CE
New Question 43:
As part of an IoT project, an organization is developing an application that will share multiple clients using a REST API.
Based on the software development process, what are two valid technical activities that can be suggested to secure the REST API that is developed during the development of the software? (Choose two.)
A. Respond to request failures in detail to allow users for easier troubleshooting.
B. Implement HTTP whitelisting to only methods that are allowed.
C. Implement and review audit logs for security-related events.
D. Reject HTTP methods that are invalid with an error code 404.
E. Implement physical firewalling and access control to the resources.
Correct Answer: BD
New Question 44:
After an application is deployed, potential issues arise around connectivity. As part of the troubleshooting process, the IP address must be determined to ensure end-to-end communication.
Which method provides the required details using the Cisco IOx CLI?
A. ioxclient application status
B. ioxclient application metrics
C. ioxclient application getconfig
D. ioxclient application info
Correct Answer: D
New Question 45:
Where are edge data services typically instantiated?
A. at the edge of the network
B. in the cloud
C. in the data center
D. in a private cloud
Correct Answer: A
…
leads4pass updates Cisco Certified DevNet Professional 300-915 exam questions and answers throughout the year and frequently shares a selection of free exam questions and answers, as shown above, candidates can improve themselves through online learning.
Also able to download the latest 300-915 dumps: https://www.leads4pass.com/300-915.html (Dumps PDF+VCE) to help them successfully pass the 300-915 Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT) certification exam on their first attempt.